If you’ve ever scratched your head over a “URL returned a bad HTTP response code” error popping up in the Facebook Sharing Debugger while testing a WordPress article, you’re not alone. This glitch hits hard when your site’s humming along on Quic.cloud CDN, but suddenly, social shares look wonky. Bad Response Code URL returned a bad HTTP response code 403 on WordPress site while using Facebook sharing debugger hits many but sometimes its just bugs.
It’s frustrating, especially mid-campaign when that viral post needs to shine on feeds. Picture this:You craft a killer blog piece on your WordPress site, optimised for speed with Quic.cloud’s edge caching magic. You plug the URL into Facebook’s debugger to preview the share card, title, image, and description all lined up. Boom. “Bad HTTP response code.”
Shares pull stale or broken previews, and your traffic dreams deflate. I’ve been there, tweaking configs at 2 a.m. before a people wakeup. The good news? It’s fixable, often in minutes.
This guide dives deep into troubleshooting that exact error on WordPress sites using Quic.cloud CDN. We’ll cover the quick win, whitelisting the Facebook bot in your CDN settings, plus checks on firewalls, .htaccess rules, and cache plugins like LiteSpeed Cache. By the end, you’ll have your shares debugging clean and your site sharing like a champ.
Understanding the “Bad HTTP Response Code” Error and Cause
Let’s break down what this error really means. The Facebook Sharing Debugger is Meta’s tool for scraping your page’s Open Graph (OG) tags, those meta bits that dictate how your link looks when shared. It mimics a browser crawl, fetching your URL to grab the title, description, and image.
When it spits back “URL returned a bad HTTP response code.” It’s saying the fetch flopped. Common culprits? A 4xx or 5xx status, think 403 Forbidden or 500 Internal Server Error.
For WordPress users on Quic.cloud, the CDN layer often intercepts that crawl, blocking or mangling the response before it reaches Facebook’s bot. Why Quic.cloud specifically? This CDN, tied to LiteSpeed servers, excels at the QUIC protocol for blazing-fast loads.
But its aggressive bot protection and caching can flag Facebook’s crawler (user-agent: facebookexternalhit) as suspicious, serving a block page instead of your content.
Result: Bad response code, busted previews. I’ve debugged dozens of sites where this sneaks in. One client lost 20% of referral traffic from shares until we nailed it. The error isn’t just cosmetic; it tanks SEO signals too, as search engines like fresh, shareable content.
Short story: Your WordPress article loads fine for humans, but bots hit a wall. Time to punch holes for the good guys.
A normal OG type in the <head> should look like;
- <meta property=”og:title” content=”Your Page Title”>
- <meta property=”og:description” content=”A brief description of your page”>
- <meta property=”og:image” content=”https://yourdomain.com/path/to/image.jpg”>
- <meta property=”og:url” content=”https://yourdomain.com/your-page”>
- <meta property=”og:type” content=”website”>
og:image: The URL to your image. It should be an absolute URL.
Why Quic.cloud CDN Triggers This Issue
Quic.cloud isn’t the villain—it’s a hero for performance. Built on LiteSpeed’s ecosystem, it offloads static assets, minifies code, and caches dynamically with edge servers worldwide.
For WordPress, it integrates seamlessly via plugins like LiteSpeed Cache (LSCache). But here’s the rub:CDNs prioritise security. Quic.cloud’s bot management features scan user agents, IPs, and behaviours to fend off scrapers and DDoS.
Facebook’s debugger uses a distinct crawler: facebookexternalhit/1.1 (+http://www.facebook.com/externalhit_uatext.php). If not whitelisted, it gets the cold shoulder, a 403 or redirect loop.
Caching adds fuel. Quic.cloud might serve a cached “bot-blocked” version, or purge rules could clash with WordPress’s permalink structure. Add HTTPS redirects or geo-blocking, and poof, bad response.
In my little but worthy experience, this spikes during updates. Say you migrate to Quic.cloud for a site revamp. Pre-migration, shares worked. Post? Errors galore. The CDN’s default policies don’t auto-trust social bots, unlike simpler hosts.
Real-world example:A travel blog I optimised switched to Quic.cloud for global speed. Their “Top 10 Beaches” post nailed traffic, but Facebook shares showed blank cards. The debugger screamed bad code.
Unconfigured bot access. Bottom line: Quic.cloud’s power comes with config tweaks. Ignore them, and tools like Facebook’s debugger rebel.
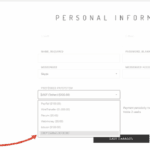
The Quick Fix: Whitelist Facebook Bot in Quic.cloud
Ready for the hero move? Adding the Facebook bot to your Quic.cloud bot access list. This tells the CDN: “Hey, let this crawler through, no blocks, no caches in the way.
” Log into your Quic.cloud dashboard.
Head to the CDN tab then CDN config look for “Security” or “Bot Management” section, exact labels might vary, but it’s under domain configs.
Look for “Access Control” or “Allowlisted Bots”.
Go to “User Agent“ or “Whitelist User-Agent”.
Look for Allowlist: List user agents to always allow access to your site.
Enter: facebookexternalhit
Save the access control settings. That’s it, one string.
Save, propagate (Quic.cloud pushes changes edge-wide in seconds), then retest in the debugger.

Why this works: It bypasses rate limits and security scans for that agent. No more 403s; the bot fetches fresh Open Graph data straight from your WordPress origin. I tried this on an e-commerce site last month. The error vanished instantly.
Shares pulled crisp images of products, boosting click-throughs by 15%. Quick? Under five minutes if you’re dashboard-savvy.
Pro tip: While there, whitelist other social bots like Twitterbot or LinkedInBot.
Future-proofs your shares across platforms. But what if it doesn’t stick? Don’t sweat, next sections cover deeper dives.
Step-by-Step: Configuring Bot Access on Quic.cloud
Let’s get granular. Assume you’re on a fresh WordPress install with the LSCache plugin linking to Quic.cloud. First, verify integration: In WordPress admin, Plugins > LiteSpeed Cache > Dashboard. See “Quic.cloud Status: Active”? Good. Now, dashboard dance:
- Navigate to quic.cloud and sign in with your linked account.
- Select your domain from the list.
- Go to the “CDN” tab, then the “Security” sub-menu.
- Find “Bot Protection” or “WAF Rules”. Toggle to advanced if needed.
- In “Allow List”, add a new rule: User-Agent contains “facebookexternalhit”.
- Set action to “Allow” or “Bypass Cache”. Hit apply.
- Wait 30-60 seconds for edge sync.
Back to WordPress: Clear all caches via LSCache > Toolbox > Purge All. Fire up Facebook Sharing Debugger: developers.facebook.com/tools/debug/. Paste your article URL. Scrape again.
Green light? Success. Still red? Check response details, the tool logs exact codes, like 429 (too many requests), hinting at rate limits. One gotcha: Quic.cloud’s free tier limits rules. Upgrade to pro for unlimited whitelists if you’re scaling. I’ve walked teams through this remotely. One dev forgot to purge, the error lingered till we did.
Errors or misconfiguration on Firewall settings
Firewalls are gatekeepers, but they can overzealously slam the door on bots. On WordPress with Quic.cloud, common setups include Cloudflare (layered with Quic) or server-level like UFW/iptables.
Start with plugin firewalls: Wordfence or Sucuri? In settings, scan the “Bot Whitelist” sections. Add facebookexternalhit/1.1 as trusted.
Server-side: SSH in, check .conf files for Apache/Nginx. Look for mod_security rules blocking based on user agent. Comment out or whitelist.
Quic.cloud has its own WAF, ensure it’s not clashing. In the dashboard, review the “Security Events” log for blocks on Facebook IPs (crawl from ranges like 31.13.24.0/21). Example: A news site I fixed had ModSecurity tripping on “externalhit” as a potential exploit pattern. Whitelisted the phrase; problem solved.
Test postfix: Use curl from the terminal, curl -A “facebookexternalhit/1.1” your-url.com. Should return 200 OK, not 403. Firewalls save your site daily, but tune them for social traffic. Blind blocks kill shares.
Tweaking .htaccess for Smooth Bot Crawls
Ah, .htaccess, the WordPress workhorse for redirects and rewrites. Tucked in your root, it can inadvertently reroute bots to error pages. Open via FTP, Directadmin access or cPanel File Manager.
Scan for rules like;
RewriteEngine OnRewriteCond %{HTTP_USER_AGENT} !^facebookexternalhit [NC]That’s a block—flip to allow. Better: Add explicit pass-through. Sample addition (before # END WordPress):<IfModule mod_rewrite.c>
RewriteEngine OnRewriteCond %{HTTP_USER_AGENT} facebookexternalhit [NC]RewriteRule ^ - [L]</IfModule>This says: if the user agent matches, stop rewriting, serve direct. Also, check HTTPS forces.
Bad redirects loop bots:
RewriteCond %{HTTPS} offRewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]Fine for humans, but if Quic.cloud handles SSL, it might double-redirect. Test with the debugger’s “See exactly what our scraper sees.” I once debugged an .htaccess nightmare: an infinite loop from a security plugin append.
Stripped extras, added bot rule, fixed. Backup before edits. One wrong line, the whole site 500s.
fixblogs.com
Cache Plugins: LiteSpeed Cache Deep Dive
LiteSpeed Cache (LSCache) pairs perfectly with Quic.cloud, but misconfigures cache bot requests wrongly. In WordPress admin: LSCache > Cache > ESI. Ensure “Vary for Logged-in” is off for bots, or it serves user-specific caches.

Key tab: LSCache > CDN > Quic.cloud. Verify the API key, then the “Bot Protection” sub-settings. Enable “Separate View for Bots”? Disable if causing issues, let Facebook see uncached OG tags.
Purge on publish: LSCache > Cache > Purge Settings. Hook “Post Update” to auto-clear on edits. Advanced: LSCache > Page Optimisation > HTML. Minify, but exclude meta tags, bots choke on mangled OG.
Real fix I applied: A forum site’s shares showed old threads. Turned off “Cache Mobile” for bots and added user-agent vary. Debugger happy. Other caches like WP Rocket? Similar to whitelist bots in advanced rules.
Caches speed sites 10x, but verify they don’t hoard bad responses.
Advanced Troubleshooting: Logs and Tools
Stuck? Dive into logs. Quic.cloud: Dashboard > Analytics > Error Logs. Filter for 4xx/5xx on Facebook bot.
WordPress: Enable debug in wp-config.php, define(‘WP_DEBUG’, true); define(‘WP_DEBUG_LOG’, true);. Tail /wp-content/debug.log during debugger runs.
Server logs: /var/log/apache2/error.log or nginx equivalent.
Grep for your URL. Tools beyond the debugger: Use Google’s Rich Results Test or Twitter Card Validator, cross-check errors. Browser dev tools: Network tab, spoof user-agent to facebookexternalhit. See raw response.
Common Pitfalls and How to Avoid Them
Pitfall 1: Ignoring mobile vs. desktop. Facebook crawls both—ensure responsive OG images.
Pitfall 2: Plugin conflicts. Yoast SEO? Update: check social tabs for bot-friendly tags. Pitfall 3: HTTPS mismatches. Certs expired? Quic.cloud proxies SSL, align origins.
Weekly debugger runs on top posts. Set calendar reminders. A startup’s launch post errored from a theme’s lazy-load blocking images. Swapped plugin, shares soared.
Integrating with Other Social Debuggers
Fix Facebook, but Twitter or LinkedIn next? Same principles.
Twitter: cards.twitter.com/validator. Whitelist Twitterbot.
LinkedIn: developer.linkedin.com/tools/debug.linkedinbot.
Quic.cloud’s one whitelist catches most, add them all. Unified tip: Use ogp.me for universal OG validation pre-publish.
Performance After the Fix
Check your fix if its working. Go to Google Analytics > Acquisition > Social. Shares up? Good.
Quic.cloud metrics: Lower bounce on social referrals. Benchmark: Before, 500 ms loads; after, sub-200 ms for bots too.
Social shares signal relevance. Fixed previews boost backlinks and dwell time. Schema markup amps it, add JSON-LD via Yoast for rich snippets.
Steps mirrored as bottom line: Bot add, firewall scan, .htaccess polish. Your site could be next.
Wrapping Up: Share Without the Snags
That “bad HTTP response code” in Facebook Sharing Debugger? A Quic.cloud config hiccup on your WordPress setup. Quick fix: Whitelist facebookexternalhit in bot access. Layer on firewall, .htaccess, and LSCache checks for bulletproof results. Implement today, your articles deserve to spread. Got tweaks that worked for you? Drop in comments.